Creating a Federated Identity Provider (IDP)
This page describes how to set up a new federated identity provider connection in the AXN. ID DataWeb supports the OpenID connect protocol. As a prerequisite, you should first set up a new IDP connection with your federated SSO provider, like Ping, Auth0, Okta, Microsoft Azure AD, or others. You will use the details from your IDP to set up a connection with ID DataWeb, as described below.
There are two main use cases for this:
- Add federated SSO to AXN Admin Setup SSO to AXN Admin
- Add an IDP to your Verification Workflow
For both use cases, the first step is adding an IDP connection via AXN Admin.
Add New Federated Identity Provider
To start, navigate to the Identity Provider link on the left navigation menu.
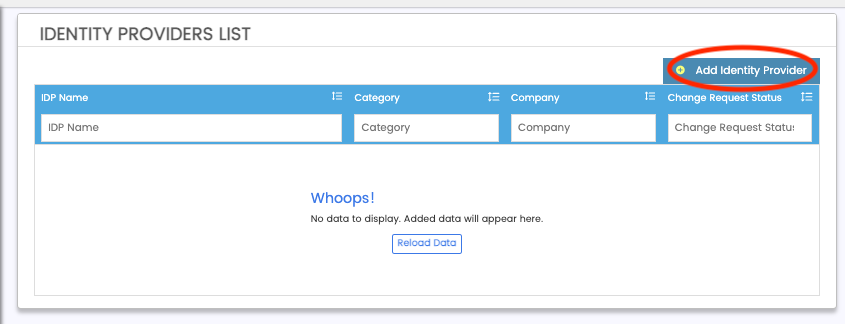
Next, click "Add New Identity provider"
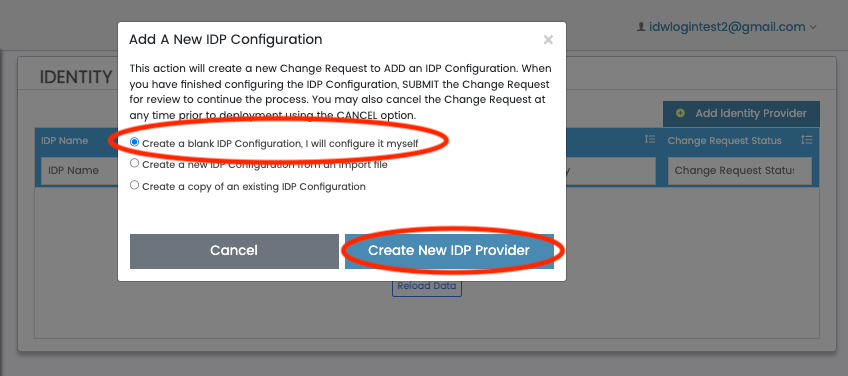
Lastly, select "Create a blank IDP Configuration, I will configure it myself", and click "Create new IDP Provider". This will bring you to the IDP Configuration screen.
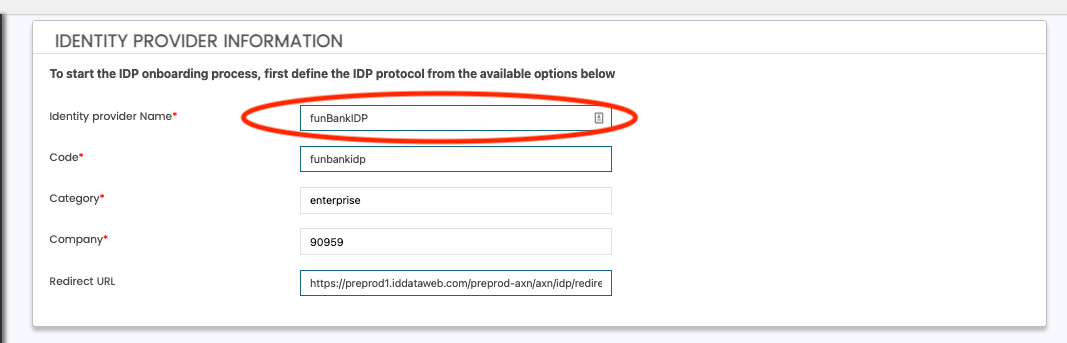
Configure a new IDP
There are two sections to the IDP setup - Identity Provider Information, and Company IDP Information.
Identity Provider Information
- Create a name for your IDP connection. For example - "funBankIDP"
- the "code" is auto-generated from your name.
- Lastly, the redirect URL value is what you'll need to whitelist on your IDP's side. This is the ID DataWeb URL where the user will be sent after authentication is complete.
Next, you will enter the details of your federated Identity Provider.
Company IDP Information
In this section, add your Identity Provider's details as shown below.
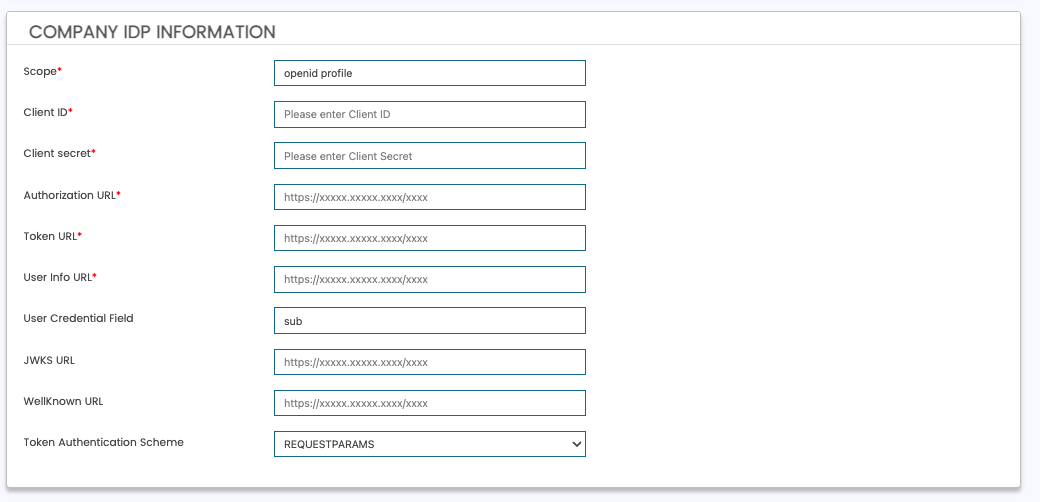
IDP Field Name | Description | Required? | Example |
|---|---|---|---|
Scope | Scopes required at your identity provider. Defaults to OpenID and Profile. Separate with space character, " " | Yes (prefilled defaults) | openid profile email |
Client ID | client_id of your identity provider. | Yes | xxyy12345 |
Client Secret | client_secret of your identity provider. | Yes | xxyy12345 |
Authorization URL | The /authorize endpoint of your OpenID Connect identity provider. | Yes | |
Token URL | the /token endpoint of your OpenID Connect identity provider. | Yes | |
User Info URL | The /userinfo endpoint of your OpenID Connect identity provider. | Yes | |
User Credential Field | Specifies how to map to the "credential" field in AXN. Defaults to "sub". If you would like to use email as the credential, this value will be "email". | Yes (prefilled default) | sub |
JWKS URL | The /jwks endpoint of your OpenID Connect identity provider. | No | |
WellKnown URL | the /well-known url of your OpenID Connect identity provider. | No | https://login.funbank.com/oauth2/.well-known/openid-configuration |
Token Authentication Scheme | Specifies how your IDP will send the client_id and client_secret during the /token request.
| Yes (prefilled default) | requestparams |
Custom URL Params
Note - this is typically not required, and can be left blank. This optional section allows you to force AXN to send additional custom URL parameters when making requests to your IDP. This can be useful for identifying AXN requests vs other applications if your IDP has not issued a new set of credentials for ID DataWeb.
To Add a new custom URL parameter, click "Add new parameter".
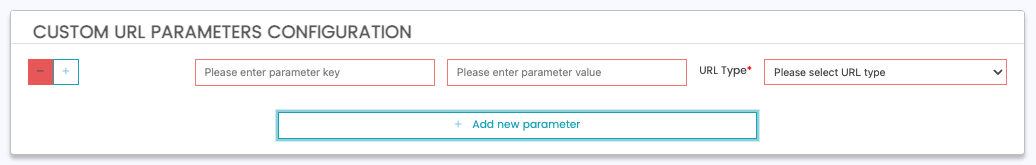
Field | Description | Required | Example |
|---|---|---|---|
Parameter Name | The name of the parameter which AXN will send. | Yes | idpRoutingFlag |
Parameter Value | The value of the parameter which AXN will send. | Yes | 123 |
URL Type | The URL which ID DataWeb will add this parameter.
| Yes | Auth URL |
In the above example, AXN will add "idpRoutingFlag=123" as a URL parameter to any requests made to your IDP. Your IDP may then use this to identity that the request is coming from ID DataWeb.
Federated Attributes Configuration
This section allows you to map additional attributes from your identity provider to AXN.
- If you are configuring an IDP For SSO to the AXN Admin portal, this step is not needed.
- If you are configuring an IDP to be used in a Verification Workflow, this can be used to prefill attributes from your IDP to the fields in an AXN Verification workflow.
To add a new attribute mapping, click "Add new attribute" button, and fill out per the description below.
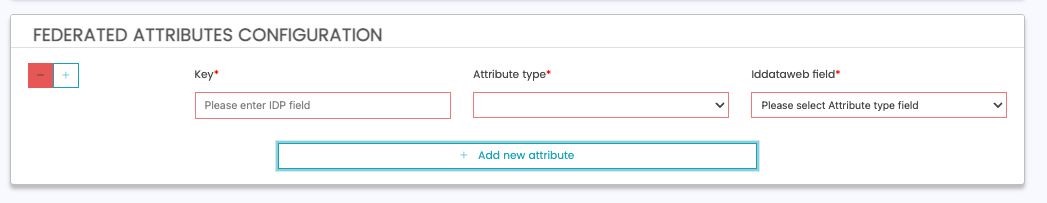
| Field | Description | Required | Example |
|---|---|---|---|
| Key | Attribute name passed from your fedrated IDP in the /token or /userinfo request. | Yes | givenName (JSON attribute key from your IDP.) |
| Attribute Type | The field you want to map this to on the ID DataWeb side. | Yes | Full Name |
| Iddataweb Field | The sub-field to map to on the ID DataWeb side. | Yes | First Name |
The above example would add the "first name" field as a mapping to ID DataWeb. In this case - the IDP's "first name" field is "givenName", and the subsequent fields map it to the fullname.firstname field on the ID DataWeb side. In this example, the administrator would also map the last name field in a similar fashion. Once complete, the full name can be mapped, prefilled and locked in an ID DataWeb verification workflow.
Saving and Deploying
Once you are done creating an IDP, you need to save and deploy to begin interacting with it.
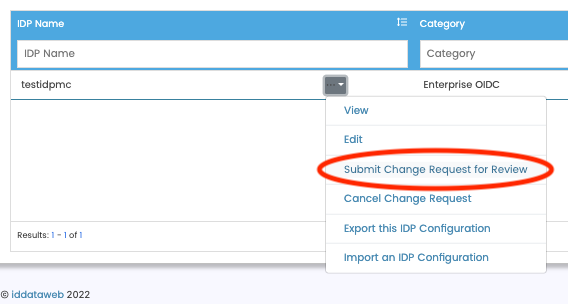
- Click "Save" on the bottom of the screen. Once saved, this will take you back to the IDP List screen.
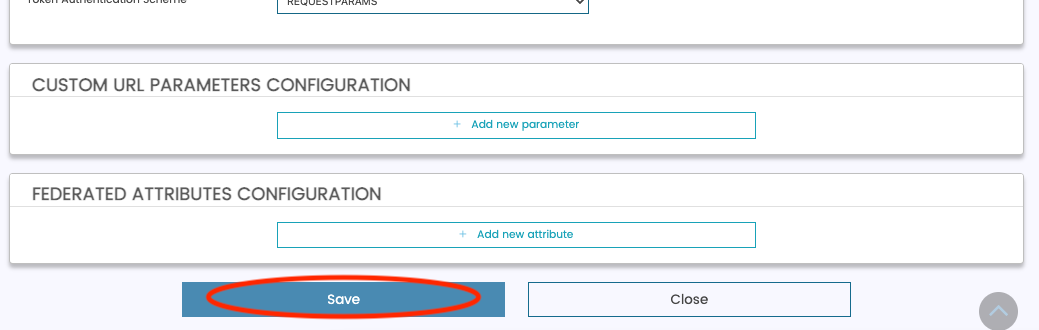
- Next, click "Submit Change Request for Review" under the "...V" button of your IDP. When the confirmation modal appears, click "Submit Change Request".
Your IDP has now been submitted. Once approved, it will be available for you to:
- Enable Enterprise SSO access to the AXN Admin console
- Add an IDP to your Verification Workflow
Add AXN Admin Redirect URL to your IDP
As a final step, you'll need to add the AXN Admin redirect URL to your IDP. This will allow your SSO system to redirect your user back to AXN Admin once they authenticate.
Updated 9 months ago
