Interpretation of Device Profiling / Session Risk
Interpreting the results of Session Risk Verification.
Overview
Device Profiling via ThreatMetrix is represented at the top level by a policy decision (true for all transactions on the AXN). You can confidently engage business logic based on only the policy decision, but understanding the underlying outcomes at the assertion and component levels will enable you to engage in more nuanced business logic and help users troubleshoot.
Recommended ReadingYou'll need to understand policy decisions and the process for finding and reviewing an individual transaction before attempting to analyze an individual transaction, which is what's covered here.
Assertions/Components
For standard Device Profiling, the verification process involves analyzing various risk indicators and assertions. Since there are multiple paths through which a user can pass verification and since users can be denied at any step, it's helpful to understand each underlying component independently.
Standard Device Profiling uses one policy component (level 1), the "Device high risk indicator" component, which is based on multiple assertions. Each assertion provides specific information about the device's risk level.
Device Profiling
TEMPLATE: Device Profiling - Risk Indicators
All of these assertions must pass for this level 1 component to pass.
| Description | Assertion Name | Component Name (Level 1) |
|---|---|---|
| Low location accuracy due to aggregator detection | detect.aggregator | TEMPLATE: Device Profiling - Risk Indicators |
| Low location accuracy due to malware detection | detect.malware | TEMPLATE: Device Profiling - Risk Indicators |
| Low location accuracy due to Tor network detection | detect.tor | TEMPLATE: Device Profiling - Risk Indicators |
| Low location accuracy due to Tor node detection | detect.torNode | TEMPLATE: Device Profiling - Risk Indicators |
| Low location accuracy due to anti-replay check | test.apSessionIDNotReplay | TEMPLATE: Device Profiling - Risk Indicators |
| Low location accuracy due to OFAC IP blacklist | blacklist.ofacIP | TEMPLATE: Device Profiling - Risk Indicators |
Interpretation & Example Outcomes
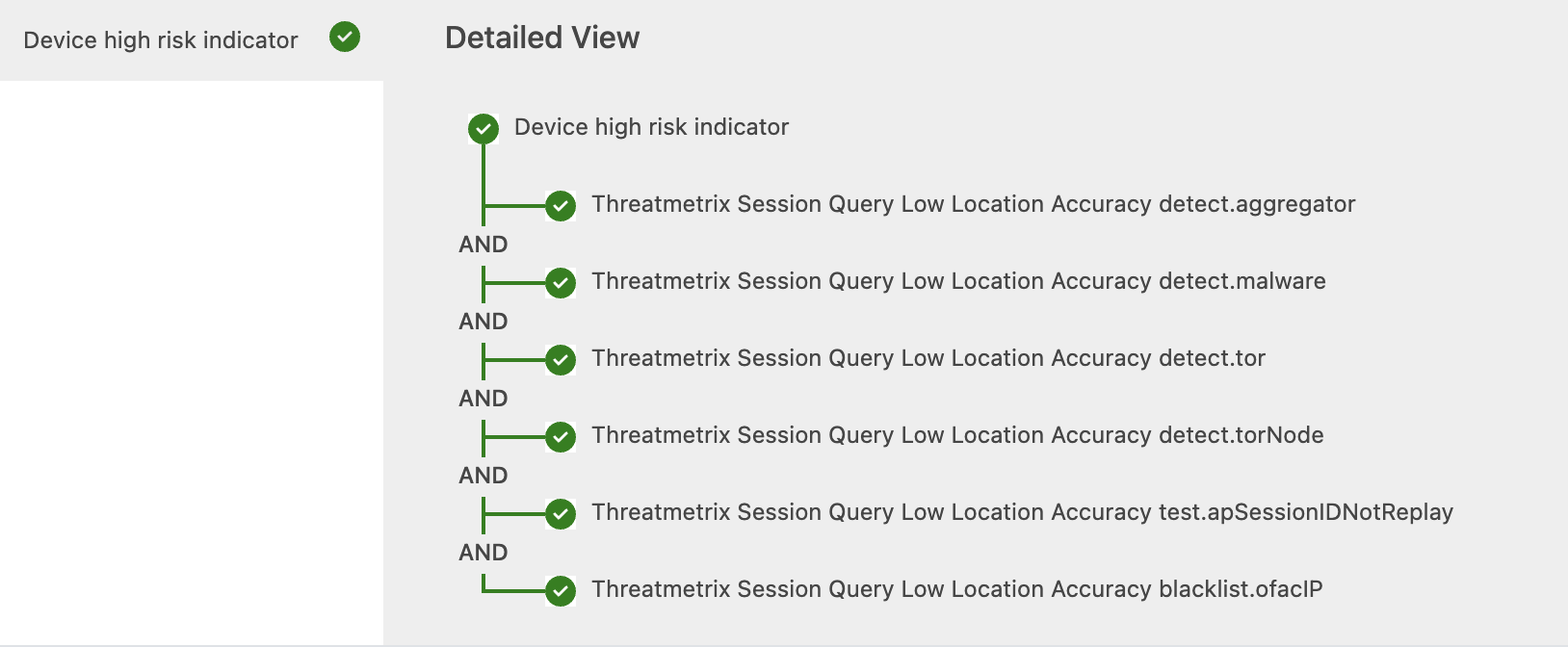
An example of a user passing the Device Profiling step with all risk indicators showing no issues.
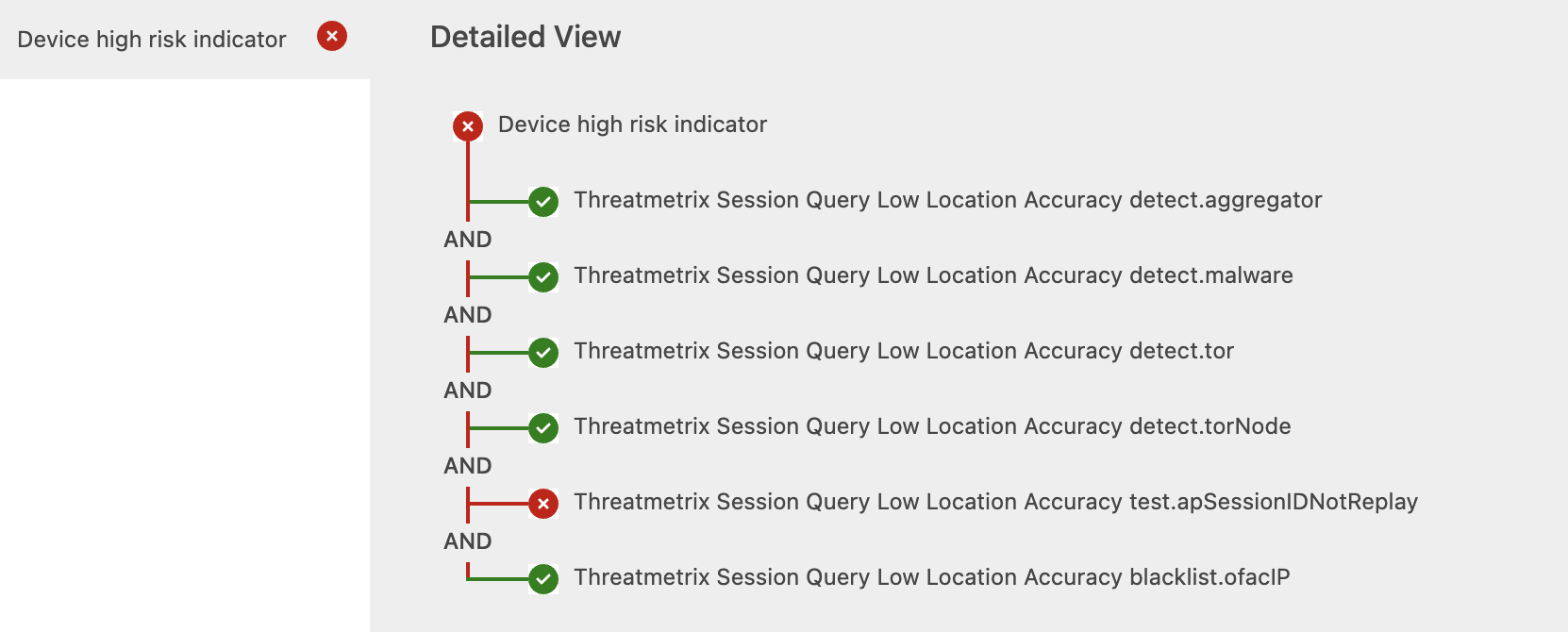
An example of a user failing the Device Profiling step due to detection of session replay.
| Result | Explanation | Solution |
|---|---|---|
| Pass | All assertions passed, indicating no high-risk indicators. | No action needed. |
| Fail | One or more assertions failed, indicating potential high-risk indicators. | Investigate the specific assertion(s) that failed and take appropriate actions. |
| Fail | Low location accuracy due to malware detection. | Advise user to scan their device for malware. |
| Fail | Low location accuracy due to Tor network detection. | Check if the user is intentionally using Tor for privacy. |
Updated 9 months ago
